Cisco Router Password Crack
Cisco Router Password Recovery - 4.0 out of 5 based on 27 votes. Password recovery is a fairly frequently used procedure for administrators and engineers. Even though we usually stack our passwords in some word, excel or text file, it's very easy to forget to update them when changes occur. To login with the modem Cisco DPC3848VM you will need to use the following default username and password: user/blank Router Ip address Others IP addresses used by the router brand Cisco.
Most routers and switches by Cisco have default passwords of admin or cisco, and default IP addresses of 192.168.1.1 or 192.168.1.254. However, some differ as shown in the table below.
Change the default login data once you're in to make your router more secure.
Cisco Default Passwords (Valid September 2019)
If you don't see your Cisco device or the default data below doesn't work, see below the table for more help, including what to do.
[1] The Cisco SFE1000P switch's default IP address is assigned via DHCP, meaning that it's different depending on the network that it's installed on. To determine the IP address for your SFE1000P, log in to the router or DHCP server that assigned the dynamic IP and look for it in the list of attached devices.
Cisco Router Password Crack
[2] The Cisco Valet M10 & Valet M20 routers are supported by Linksys. Cisco owned Linksys from 2003 through 2013 and branded the Valet routers with the Cisco name and logo. See our Cisco Valet M10 & Valet Plus M20 default password and support info page for more details.
If your Cisco device isn't listed in the table above, let us know. We'll look up the default login information for it and add it to this list.
Next Steps If the Cisco Default Login or IP Above Doesn't Work
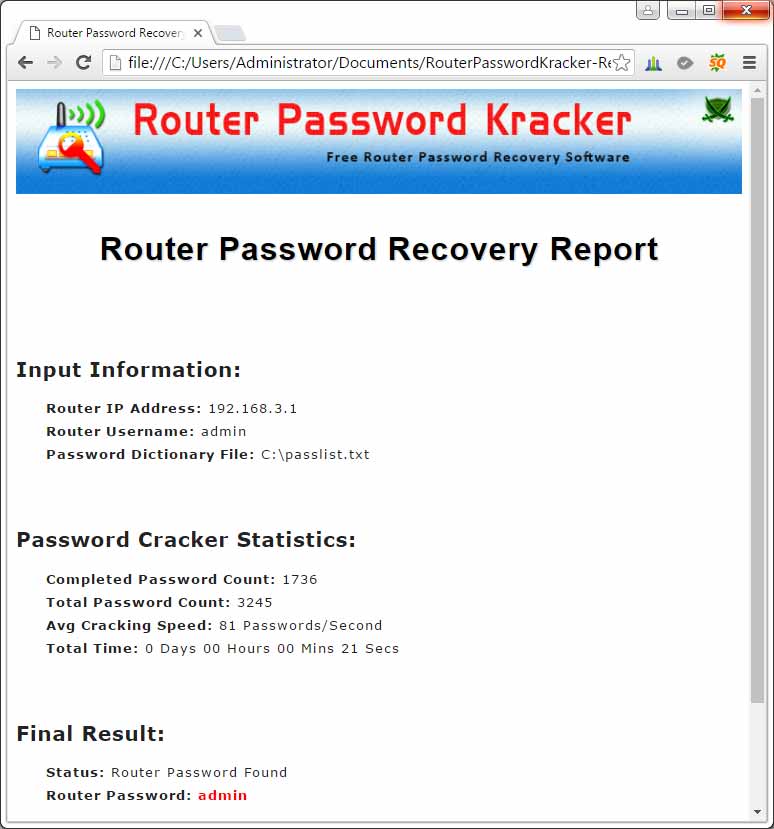
If the default username or password doesn't work, it means that it's been changed.
Unlike residential routers, the Cisco business and enterprise-class routers and switches have specific password recovery features, meaning that a full factory reset (the typical reset-a-password process) isn't required.
If you can't locate the password recovery steps for your device, Cisco Support has a PDF manual for every device, which includes help in this area, too.
Most network devices operate with the default IP address they come with but routers, and especially switches, in business and enterprise environments, are often changed when installed. Learn how to identify network hardware IP addresses on a local network if the default IP isn't working.
Today’s life is so fast and hectic and each day we learn something new in our professional or personal life. We have to remember so many things like cell number, debit/credit card PINs, Email/Facebook/mobile and many more passwords to keep things in a flow. But network engineers have to remember the above-mentioned details as well as network details, also. They have to keep in mind all the IP schemes, routing-switching protocol details, and security details of their network devices which they are using currently in an organization. Routers play a core role in inter-networking; What if you forget the router’s password? Then your life will become hell, because without the password you are not able to access your router, so if anything goes wrong within the network you won’t be able to monitor or change it. Wait; don’t be afraid that this document describes how to recover the enable password and the enable secret passwords. Router’s password recovery is a very common procedure and should be known by any CCNA without referring to documentation.These passwords protect access to privileged EXEC and configuration modes. The enable password can be recovered, but the enable secret password is encrypted and must be replaced with a new password. Use the procedure described in this article in order to replace the enable secret password. The information in this article is based on this hardware version: the Cisco 2600 Series Router, which is by far the most popular router used in lab environments as well in industry. You also can use the recovery steps on other Cisco routers.
This password recovery procedure works for the following Cisco products:
Cisco 806, 827, uBR900, 1003/4/5, 1400, 1600, 1700, 2600, 3600, 3700, 4500, 4700, AS5x00, 6×00, 7000 (RSP7000), 7100, 7200, 7500, uBR7100 series routers.
The passwords for a router are stored in the startup-config file in NVRAM. Recovering the password involves “breaking in” during the router boot-up process and configuring the configuration register so that the startup-config file is bypassed. This allows the router to start in an unconfigured state with no password. From that point, the network administrator again has control of the router and can both recover configuration information and reset the password
First, hook up the DB9 end of the standard light blue serial cable to your serial port. The other end of the cable should plug into the port labelled “Console” on the back of the Cisco router. If you do not have a serial port, then you’ll need to go purchase a USB-to-serial adapter cable and install it on your computer.
Now that your hardware is connected, establish a serial connection with the router. On Windows, I use putty for this connection. Yes, putty can be used to make serial connections as well as telnet/ssh. Hyperterminal works great as well. On Linux, I use minicom and on FreeBSD/OpenBSD, I use cu (cu -s 9600 -l /dev/cuad0).
Reboot the router and press the Break key to interrupt the boot sequence.
After that, Type confreg 0x2142. This tells the router to bypass NVRAM during bootup. In other words, your existing configuration won’t be loaded. The good news is that it won’t be deleted either.
Type reset to reboot the router. Answer No when prompted to run setup.
Type copy start run. This loads your start-up configuration into memory. Now, if you type a show run config, you’ll see the router configuration. Also, you should notice that your router name is now in the prompt instead of the default “Router”.
Change the enable secret – “enable secret new_password”
Change the register back to 0x2102:
config-register 0x2102
When the router reboots it will load the old configuration with the new password.
Save the password so that it will be persistent during reboots, type copy run start
Reboot the router by typing reload at the enable prompt. I think you now need some practical information. Shown below is a Cisco 2651XM router that has a console password on the device. With such a password, you cannot access exec mode without authenticating this password correctly. When buying routers used, you may commonly be faced with this scenario.
Consider following steps to understand in more convenient way
Step 1. Power cycles the router or power on the router initially. While the router is booting, you’ll need to break the boot sequence to boot the router into boot ROM; you do this by holding down CTRL and pressing PAUSE BREAK. Do this repeatedly till you are placed at the boot ROM prompt.
Step 2. Change the configuration register so that the router will ignore the contents of the NVRAM when booting into Cisco IOS. Set the configuration register to 0×2142 and boot the router.
Step 3 (Option 1) – After the router has booted into Cisco IOS, you’ll be prompted by the initial configuration dialog; type n here and press enter and you’ll be placed into user mode. Now you’re able to place yourself into privileged mode by typing enable. Once in privileged mode, you can copy the startup configuration to the running configuration and then change the passwords manually then saved the configuration by to NVRAM by typing copy run start.
Step 4 (Option 2)
– After the router has booted into Cisco IOS, you’ll be prompted by the initial configuration dialog; type n here and press enter and you’ll be placed into user mode. Now you’re able to place yourself into privileged mode by typing enable. Once in privileged mode, you can erase the contents of NVRAM by issuing the write erase command.
Step 5. Once you’ve performed a password reset or NVRAM sanitation, you’ll need to set the configuration register back to 0×2102 so the router will boot normally and load the NVRAM contents upon a reboot or power failure.
Now I show what I did when I forget the enable password. I enter a guess password three times:
Router>enable
Password:
Password:
Password:
% Bad secrets (I got this message after entering wrong password three times again n again)
Cisco Wireless Router Password Reset
Then I Reboot the router and press the Break key to interrupt the boot sequence.
rommon 1 > confreg 0x2142
Cisco Router Password Change
You must reset or power cycle for new config to take effect
rommon 2 > reset
— System Configuration Dialog —
Self decompressing the image: ###############################
############################### [OK]
Would you like to enter the initial configuration dialog? [Yes/no]: n
— System Configuration Dialog —
Router>
Router>enable
Router#copy startup-config running-config
Destination filename [running-config]?
1324 bytes copied in 2.35 secs (662 bytes/sec)
Router#
Router#configure terminal
Router(config)#enable secret < password >
Router(config)#^Z
Router#configure terminal
Router(config)#interface Ethernet0/0
Router(config-if)#no shutdown
Router#copy running-config startup-config
Router#configure terminal
Router(config)#config-register 0x2102
Router(config)#^Z
00:03:20: %SYS-5-CONFIG_I: Configured from console by console
Router#show version
— System Configuration Dialog —
Configuration register is 0x2142 (will be 0x2102 at next reload)
Now you can access your router as usual and no need to fear at all when you forget or lose a Cisco router’s password. Password recovery is a very basic requirement for a CCNA person, I could complete this article within 20 lines but I know the importance of password recovery for any level of network engineer. That’s why I have given you password recovery method with very broad description. Thanks for giving me your time by reading this article. If you have any queries or anything to say feel free to use the comment box below.
References:
- Guide to Cisco Certified Network Associate certification by Todd Lamlee, Sybex press.
- Guide to Cisco Certified Network Associate by Richard Deal.
- www.cisco.com/image/gif/paws/22188/pswdrec_2600.pdf